Don't miss out on the latest updates.
Fill in your email address to stay informed about upcoming training sessions, events, and testing know-how.
Blog
As of early 2024, GitHub has become the largest platform for code hosting, boasting over 100 million developers and more than 372 million repositories. This significant growth underscores GitHub's pivotal role in the global development community, enabling extensive collaboration and project management for developers worldwide.
Application security remains a top priority for developers. The 'shift left' strategy, which involves integrating security measures early in the development process, is crucial for maintaining both security and developer efficiency. GitHub supports this approach through tools like CodeQL and its marketplace, facilitating early detection and resolution of potential security issues.
Doing security analysis on source code right when it gets committed seems like a natural way to do source code repositories. in 2019, GitHub acquired Semmle with the idea of incorporating their static code analysis technology into the platform. A year later, the technology got fully integrated into GitHub, made compatible with GitHub Actions (GitHub continuous integration / continuous delivery mechanism) and GitHub marketplace, and launched as GitHub code scanning.
Code scanning is free for public repositories and is a GitHub Advanced Security feature for GitHub Enterprise.
To enable it, simply go to the Security tab of your code repository:
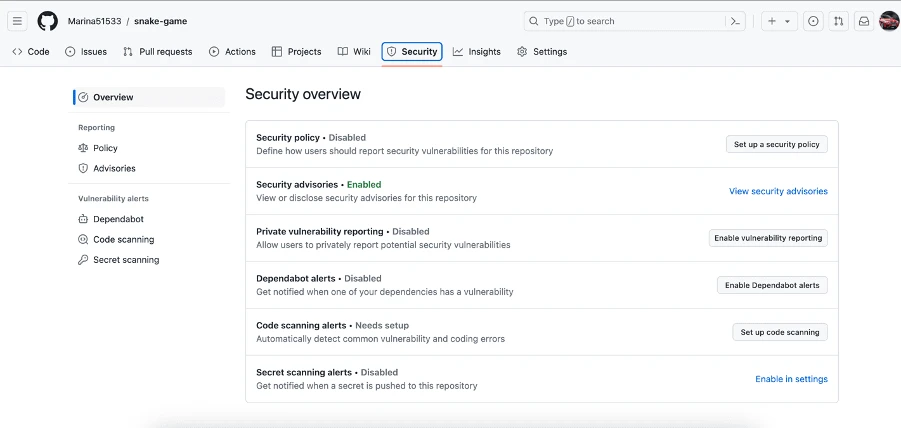
Set CodeQL policy:
Set all necessary configuration for your project:
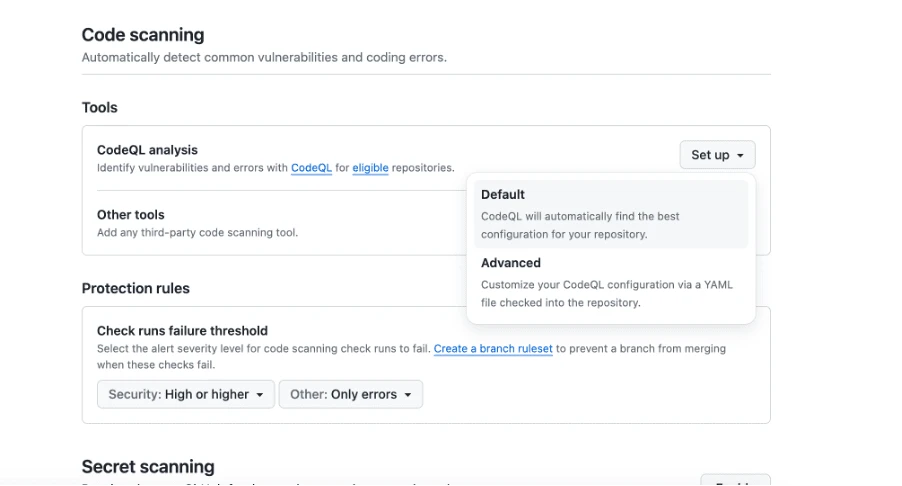
Select the alert severity for code scanning:
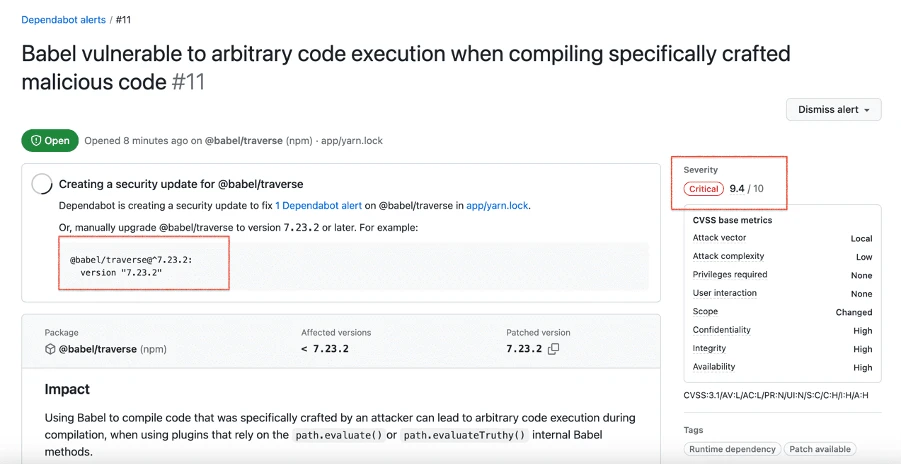
When GitHub's code scanning detects a potential vulnerability or error in your code, it generates an alert within the repository. Once you correct the issue that triggered the alert, GitHub automatically closes the alert.
CodeQL uses a query language known as QL, which is an object-oriented logic programming language. This query language allows CodeQL to analyze and understand the structure and behavior of your code.
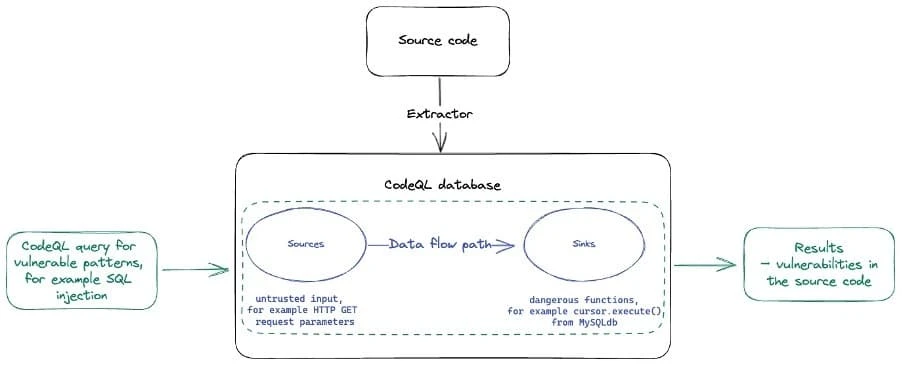
While CodeQL primarily identifies security vulnerabilities, it doesn't directly fix them but excels at highlighting where the issues lie. This makes it easier for developers to address the weaknesses.
Initially, CodeQL would flag potential issues for developers to investigate and fix. However, with the introduction of the Autofix feature, the process is enhanced by AI. This functionality allows the tool not only to detect problems but also to suggest appropriate code modifications to address them directly.
The Autofix feature integrates the capabilities of CodeQL with GitHub Copilot, another AI-powered tool. CodeQL scans the codebase for vulnerabilities, while Copilot leverages machine learning to generate potential fixes. These suggestions are then presented to the developer for review and approval.
Vulnerability alerts in GitHub repository are sorted from Low to Critical:
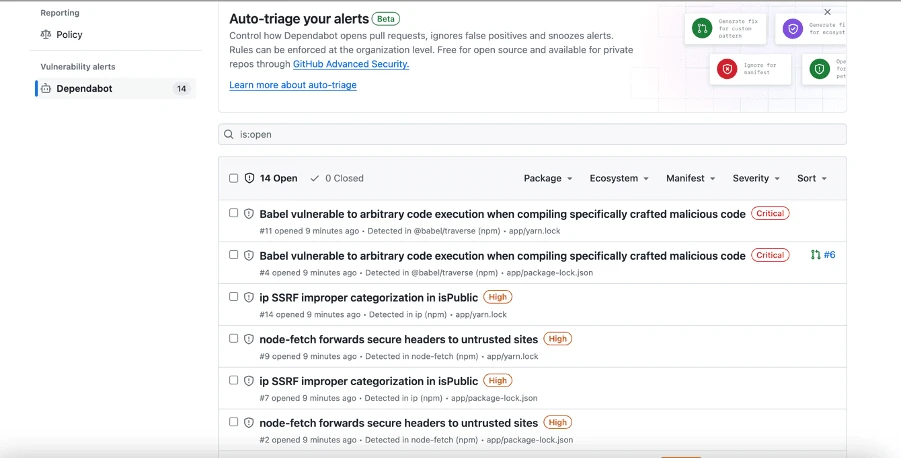
You will be able to fix issue manually or to use Autofix:
This innovative tool offers many benefits for developers and development teams:
Criteria | CodeQL | SonarQube | Checkmarx |
Analysis approach | Semantic code analysis using a query language to treat code as data | Static code analysis with continuous inspection | Static and dynamic code analysis |
Language support | Supports multiple languages including C/C++, Java/Kotlin, JavaScript/TypeScript, and more | Supports 30+ languages including Java, C#, JavaScript, TypeScript, Python, and PHP | Supports 30+ languages including Java, C#, JavaScript, TypeScript, Python, and PHP |
Vulnerability detection | High precision with detailed security queries | Broad coverage with an emphasis on code quality and security vulnerabilities | Comprehensive security vulnerability detection including OWASP Top 10 and SANS 25 |
Customizability | Highly customizable with the ability to write custom queries | Customizable rules and profiles, extensible with plugins | Extensive customization options, allows custom queries and rules |
Autofix capabilities | Offers AI-powered autofix for certain vulnerabilities | Provides suggestions but limited autofix capabilities | Limited autofix capabilities, focuses more on detection and reporting |
Learning curve | Moderate to high; requires understanding of its query language (QL) | Moderate; user-friendly interface with extensive documentation | Moderate; extensive documentation and training materials available |
Cost | Free for public repositories on GitHub; paid plans for private repositories and enterprise features | Open-source with paid options for enterprise features | Commercial product with different pricing tiers based on the size and needs of the organization |
Link | CodeQl | SonarQube | Checkmarx |
I started using CodeQL a few months ago and quickly realized how useful and user-friendly this tool is. As someone who prioritizes code protection and aims to keep my code free of vulnerabilities, CodeQL has been invaluable. Its ability to analyze code and identify potential security issues helps ensure that my projects are clean and secure.
One feature I particularly appreciate is Autofix, which simplifies the developer's job by automatically suggesting fixes for detected vulnerabilities. However, if you prefer to handle fixes manually, CodeQL accommodates that as well, giving you the flexibility to address issues in your own way.
Overall, I would highly recommend CodeQL to anyone who is serious about cybersecurity and wants a reliable tool for maintaining robust code security.
Don't miss out on the latest updates.
Fill in your email address to stay informed about upcoming training sessions, events, and testing know-how.
Need Advice?
Request our free, non-sales consultation. Fill out the form and we will get back to you.
Watchdog
Did not find a date that works for you? ....
Notice